Cyber Security Training in Pakistan | Importance, Ethical Hacking & Pen Testing
Aaj ki dynamic digital world mein, jahan hamari zindagi, businesses, and critical infrastructure interconnected systems par depend karte ha, cyberattacks ka threat pehle se zyada acute ho chuka hai. Data breaches jo millions devices ko affect karte hain se le kar ransomware attack prevention tak, digital vulnerabilities ki exploitation ab ek global security concern ban chuki hai.
Pakistan ke liye, jo fast-paced digital transformation se guzar raha hai, apni online presence aur sensitive data protection sirf technical challenge nahi balkay ek strategic imperative hai. Digital assets and information systems ki security, economic stability, national security, aur public trust ke liye extremely essential hai.
Ye barhta hua threat ek specialized aur high-demand field ko promote kar raha hai: Ethical Hacking and Penetration Testing. Aaj ke era me ye sirf aik option nahi balkay ek majboori ban chuka hai. Har organization ko apni security posture ko evaluate karna, khud apne systems ko ethically hack karna, aur vulnerabilities ko patch karna zaroori hai is se pehle ke ye flaws kisi black hat hacker ke haath lag kar data breach, ransomware attack, ya financial loss ka sabab ban jayein. Proactive cyber risk assessment aur vulnerability management hi wo defensive shields hain jo aaj ki connected duniya me survival ki guarantee ban sakte hain.
Aaj ke barhte hue cybersecurity threats ke dor mein, zaroori hai ke hum sirf digital consumers na rahain, balkay apni cybersecurity skills ko develop karke is digital ecosystem ke proactive defenders banai kyunke aaj ka daur ek silent cyber war ka hai, jahan sirf wo log survive karte hain jo apne systems ko defend kerny ky sath sath cyber-attack karna b jaante hain ku ky Cyber Warrior wohi hota hai jo sirf defend karna hi nahi, balkay ethically attack karna bhi jaanta ho.
What is Ethical Hacking and Types of Hackers?
What is Hacking ? | Concept & Overveiw
Penetration Testing par discussion shuru karne se pehle, Ethical Hacking ke concept ko samajhna bohat zaroori hai. Ethical Hacking aik authorized security practice hai jisme security professionals systems, networks, aur applications ki security assessment karte hain taake unmein maujood vulnerabilities ko identify aur exploit kar ke unhe patch kiya ja sake. Is approach ka maqsad organizations ki defense mechanisms ko mazboot karna hai taake wo malicious attacks se pehle apni security ko behtar bana saken.
Ethical Hacking mein technical aur non-technical dono qisam ki techniques shamil hoti hain. Technical side mein penetration testing, vulnerability scanning, aur configuration review shamil hain. Non-technical methods mein social engineering jaise ke phishing attacks simulate karna ya sensitive maloomat hasil karne ke liye human behavior ka assessment karna shamil hai. Yeh tamam activities organization ke full consent aur legal authorization ke under ki jati hain.
Types of Hackers | Basic Classification
Cybersecurity domain mein hackers ko do fundamental categories mein classify kiya jata hai :
Black Hat Hackers and White Hat Hackers.
Aik hacker ya to malicious hota hai jo unauthorized access ke zariye nuksan pohanchata hai (Black Hat Hacker) . Ya authorized security professional hota hai jo systems ki vulnerabilities ko identify aur remediate karta hai (White Hat). Baaki tamam subcategories in do primary types ke andar behavioural aur motivational nuances ko represent karti hain. so ab Hackers ki types ko technical terms and concepts ke sath discuss karte hain:
White Hat Hackers (Ethical Hackers):
Yeh cybersecurity professionals hain jo penetration testing, vulnerability assessment, risk analysis, aur remediation strategies perform karte hain taake organizations apni security posture ko Secure aur Stable bana saken. Inka kaam puri tarah authorized hota hai aur ye industry ke standards aur compliance frameworks jaise PCI-DSS, ISO 27001, NIST, aur GDPR ko rigorously follow karte hain, jisse data security aur regulatory requirements ka poora khayal rakha jata hai.
Black Hat Hackers:
Yeh malicious actors hain jo zero-day exploits, malware deployment, aur unauthorized intrusion techniques ka istemal karte hain taake data breach, financial fraud, ya service disruption create kar saken. Inka maqsad aksar personal ya financial faida hota hai.
Grey Hat Hackers:
Yeh hybrid hackers hain jo bina explicit authorization ke security flaws identify karte hain aur kabhi kabhi un vulnerabilities ko responsibly disclose bhi karte hain. Lekin unka approach ethical boundaries ke mutabiq nahi hota, jis ki wajah se unka behaviour unpredictable hota hai.
Script Kiddies:
Yeh novices hote hain jo pre-built hacking tools aur automated scripts ka use karte hain bina deep technical knowledge ke. Inka impact limited hota ha lekin ye cyber incidents ka sabab ban sakte hain.
Hacktivists:
Yeh politically ya socially motivated threat actors hote hain jo Distributed Denial of Service (DDoS), website defacement, aur data leaks jaise attacks karke apne agenda ko promote karte hain.
State-Sponsored Hackers (APT Groups):
Yeh highly skilled cyber espionage teams hote hain jo nation-state directives ke tehat sophisticated persistent threats (APTs) launch karte hain taake national security intelligence collect kar saken ya strategic objectives achieve kar saken.
Red Hat Hackers:
Yeh proactive threat hunters hain jo black hats ke tactics ko use karte hue unke infrastructure ko disrupt karte hain, lekin kabhi kabhi inka approach aggressive ya retaliatory bhi ho sakta hai.
What is penetration testing? | What is pen testing? | Pen testing Explained
Penetration test basically ethical hacking ki aik subclass hai, jisme different methods and procedures use kiye jate hain taake organization’s security ko test and protect kiya ja sake. Penetration tests ka main purpose yeh hota hai ke wo vulnerabilities identify karein jo organization me exist karti hain, aur check karein ke kya attacker in vulnerabilities ko exploit karke kisi asset tak unauthorized access hasil kar sakta hai ya nahi.
Pre-engagement & Rule of Engagement (ROE)
What are the pre-engagement interactions in penetration testing?
Penetration tests start karne se pehle, bohot si cheezen hain jo aapko clients ke sath discuss karni hoti hain. Yeh woh phase hai jahan customer aur aapki company ka representative baith ke legal requirements aur “rules of engagement” ke bare me detail me baat karte hain.
Rules of Engagement for Penetration Testing
Penetration testing ma aik rule of engagement hota hai, jo basically define karta hai ke penetration test kaise conduct hoga, kaunsi methodology use hogi, start aur end dates kya hongi, milestones, goals of the penetration test, liabilities aur responsibilities waghera. Ye sab cheezen dono parties “ customer aur company ka representative ” ke beech mutually agree honi chahiye penetration test start hone se pahly.
Almost har ROE me ye important requirements hoti hain:
- Proper “permission to hack” aur “nondisclosure” agreement dono parties ko sign karna hota hai.
- Engagement ka scope aur organization ka kaunsa part test hoga
- Project duration, start aur end date ke sath.
- Penetration test conduct karne ki methodology.
- Penetration test ke goals.
- Allowed aur disallowed techniques, jaise ke denial-of-service testing perform karna ya nahi.
- Liabilities aur responsibilities, jo pehle se decide ki jati hain. Penetration tester ke tor par aap kabhi aise systems me access kar sakte hain jo accessible nahi hone chahiye, jisse denial of service ho sakta hai; ya aap sensitive information jaise credit cards access kar sakte hain. Isliye liabilities engagement se pehle define honi chahiye.
Agar aapko detailed documentation chahiye, to “PTES Pre-engagement” document refer karein:
What is the most important first step in a penetration test?
Defining the scope is the foundation of any penetration test. Is stage me project boundaries, objectives, timelines, and legal permissions clearly set kiye jate hain taake testing targeted, efficient aur legally compliant ho. Yehi framework baaki poore engagement ka direction decide karta .
Defining the Scope of a Penetration Test Detailed Checklist
- Project ka overall estimate karna
- Time estimation ke liye metrics
- Additional support based on hourly rate
- Questionnaires, scope creep
- Business unit managers ke liye questions
- Systems administrators ke liye questions
- Help desk aur general employees ke liye questions
- Start aur end dates specify karna
- Letter of Amendment (LOA)
- Goals section se tie back Scoping Details
- IP ranges aur domains specify karna, validate karna
- Cloud services aur ISP check karna
Dealing with Third Parties
- Acceptable social engineering pretexts define karna
- Web hosting aur MSSPs
- Countries jahan servers host hain
Milestones & Project Tracking
Defining & Tracking Penetration Testing Milestones
Penetration tests start karne se pehle, ye acha practice hai ke milestones set kiye jayein, taake aapka project rules of engagement me diye gaye dates ke mutabiq deliver ho.
Aap milestones track karne ke liye GANTT chart use kar sakte hain ya koi website jaise Basecamp, jo aapko progress monitor karne me help karti hai.
Neeche ek chart example diya gaya hai jo milestones aur unke accomplish hone ki dates define karta hai.
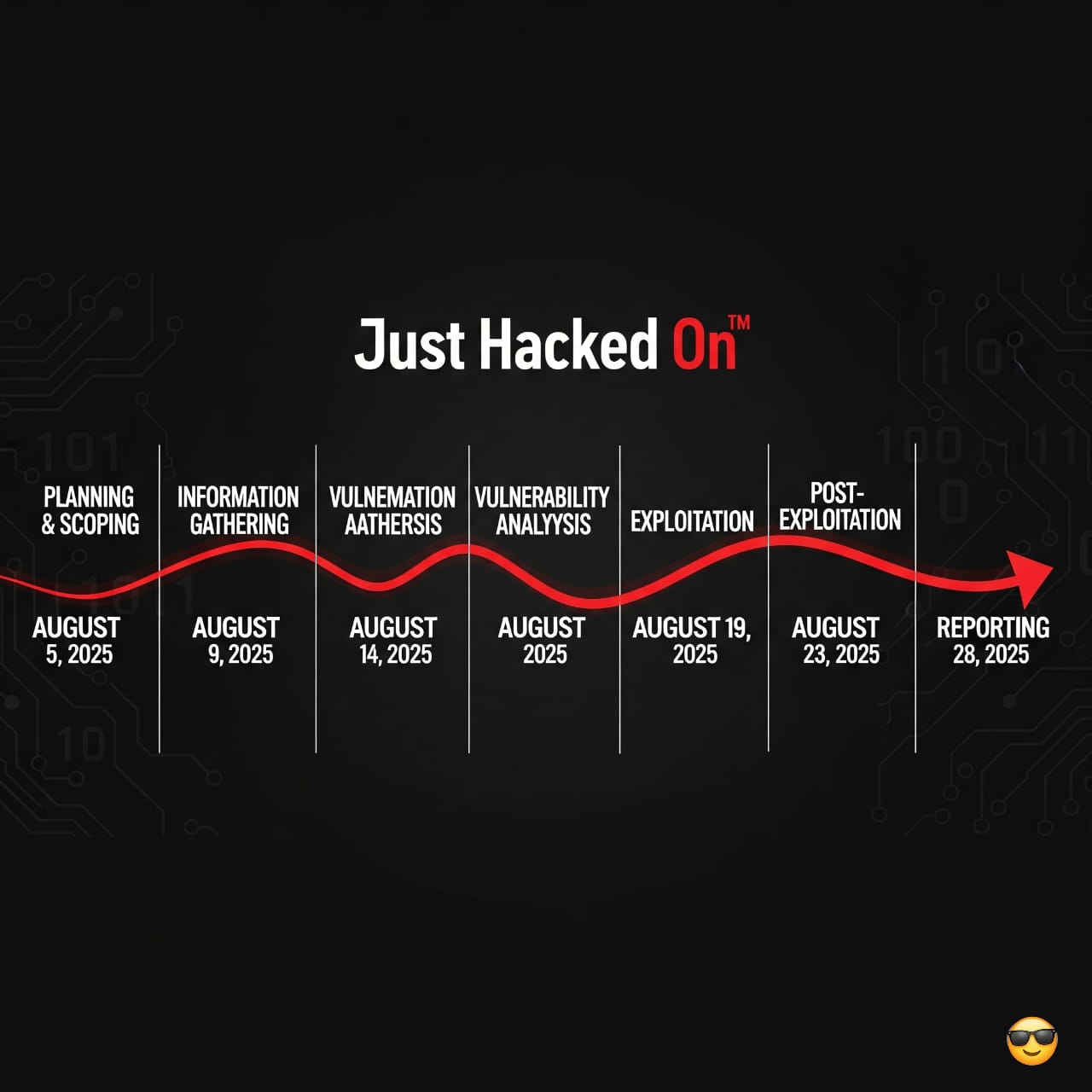
Top 3 Penetration Testing Methodologies and Standards
Penetration testing ma, methodology aur reporting sabse important steps hote hain. Pehle hum methodology ke bare me baat karte hain.
Kai different types ki penetration testing methodologies hoti hain jo define karti hain ke penetration test kaise perform kiya jana chahiye. Neeche un me se kuch ko discuss kiya gaya hai.

OSSTMM | Open Source Security Testing Methodologies Manual
What is Open Source Security Testing Methodology Manual OSSTMM?
OSSTMM basically almost har step cover karta hai jo aik penetration test me involve hota hai. Jo methodology penetration test ke liye use hoti hai, wo conceptually simple hai, lekin process khud kaafi complex hai, jiski wajah se ise daily kaam me implement karna challenging ho jata hai.
Penetration tests, chahe complex hi kyu na ho, complete hone ke liye companies ke budgets me significant payment demand karte hain , jo aksar bohot si organizations afford nahi kar pati.
Agar aap is methodology ko detail me parhna chahte hain, to official documentation ko read kerain :
Link : https://www.isecom.org/OSSTMM.3.pdf
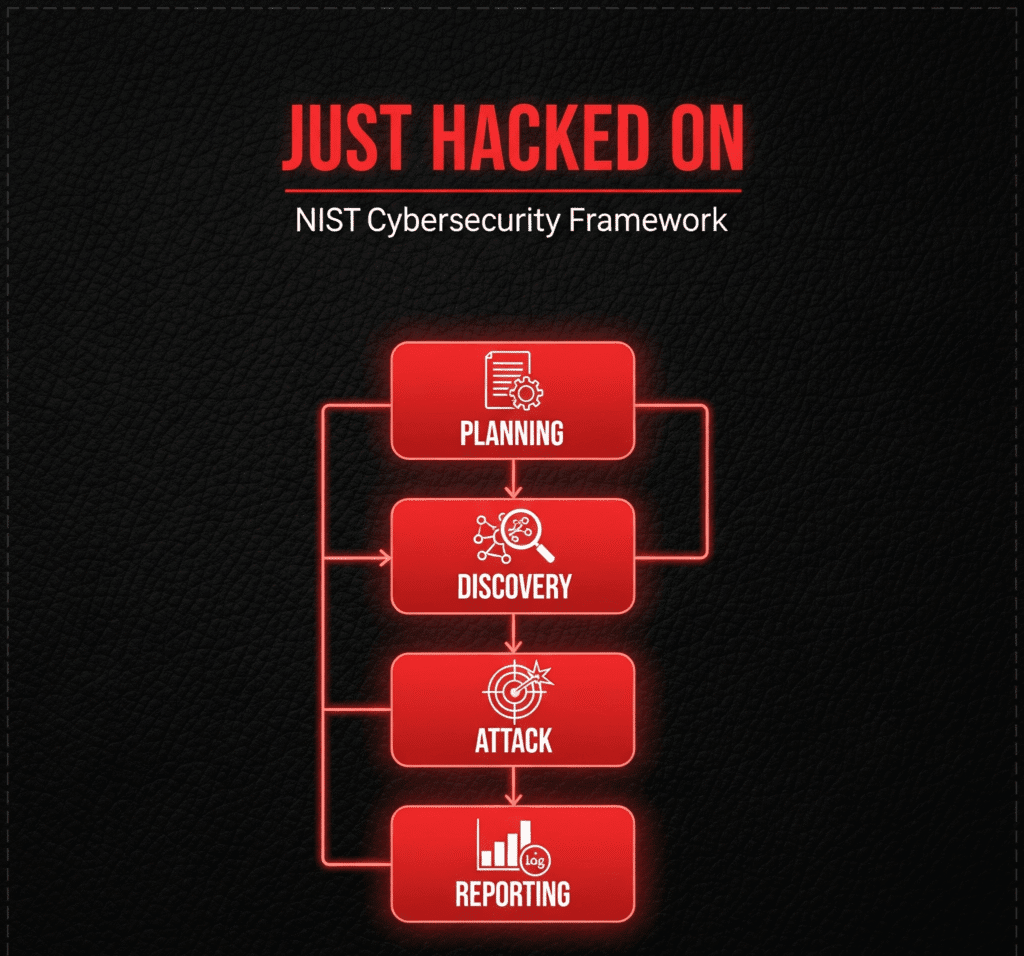
NIST Framework | 4 Core Stages
What is NIST (National Institute of Standards and Technology) and What are the 4 stages of the NIST framework?
NIST framework OSSTMM se zyada comprehensive hota hai, aur iska sabse bara faida yeh hai ke aap isko daily operations aur short-term engagements me apply kar sakte ho. Is methodology ke 4 core steps hote hain: Planning, Discovery, Attack, and Reporting.
- Planning phase me decide hota hai ke engagement ka scope kya hoga, kaise execute hoga, aur kaun se tools ya techniques use hongi.
- Discovery phase do parts me divide hota hai:
Information gathering, network scanning, service identification, aur OS detection.
Vulnerability assessment, jisme weaknesses identify ki jati hain jo exploit ho sakti hain. - Uske baad aata hai Attack phase jo har penetration test ka core hota hai. Agar is phase me aap successfully kisi target ko compromise kar lete ho aur naya host discover hota hai (jaise dual-homed systems ya multi-interface connections), to process dobara step 2 “Discovery “par return karta hai, jab tak saare potential targets cover na ho jayein.
- Reporting phase ko hum blog ky end ma overall detail sy discuss kerain gy .
NIST ka detailed version attack phase ke andar ke steps bhi cover karta hai, jaise Gaining Access, Privilege Escalation, System Browsing, aur Installing Additional Tools. In steps ko hum infuture in-depth samjhenge.” Agar aap is methodology ko detail me parhna chahte hain, to official documentation ko read kerain :
OWASP & Web Application Testing
What is OWASP? and difference between NIST and OWASP?
Agar aap ne notice kiya ho to ab tak humne jo methodologies discuss ki hain, unka focus zyada network penetration testing par tha, na ke specifically web applications ke liye. Isi gap ko cover karne ke liye OWASP Testing Methodology use hoti hai, jo web application security ke liye industry-standard approach mani jati hai. Yahi framework hum Just Hacked On me har application penetration test ke liye adopt karte hain. Aur agar aap chahein to isi process ke through, Basic se Advanced Ethical Hacking seekhte hue, aap real-world penetration testing skills develop kar sakte hain jo aapko cybersecurity industry me career shuru karne ke liye ek strong foundation deti hain.
OWASP Testing Guide me wo tamam cheezein shamil hain jo aap ek web application ko test karte waqt check karte ho. Yeh methodology bohot hi comprehensive hai aur isay industry ke kuch best web application security researchers ne design kiya hai.
Official OWASP Testing Guide: https://owasp.org/www-project-web-security-testing-guide/
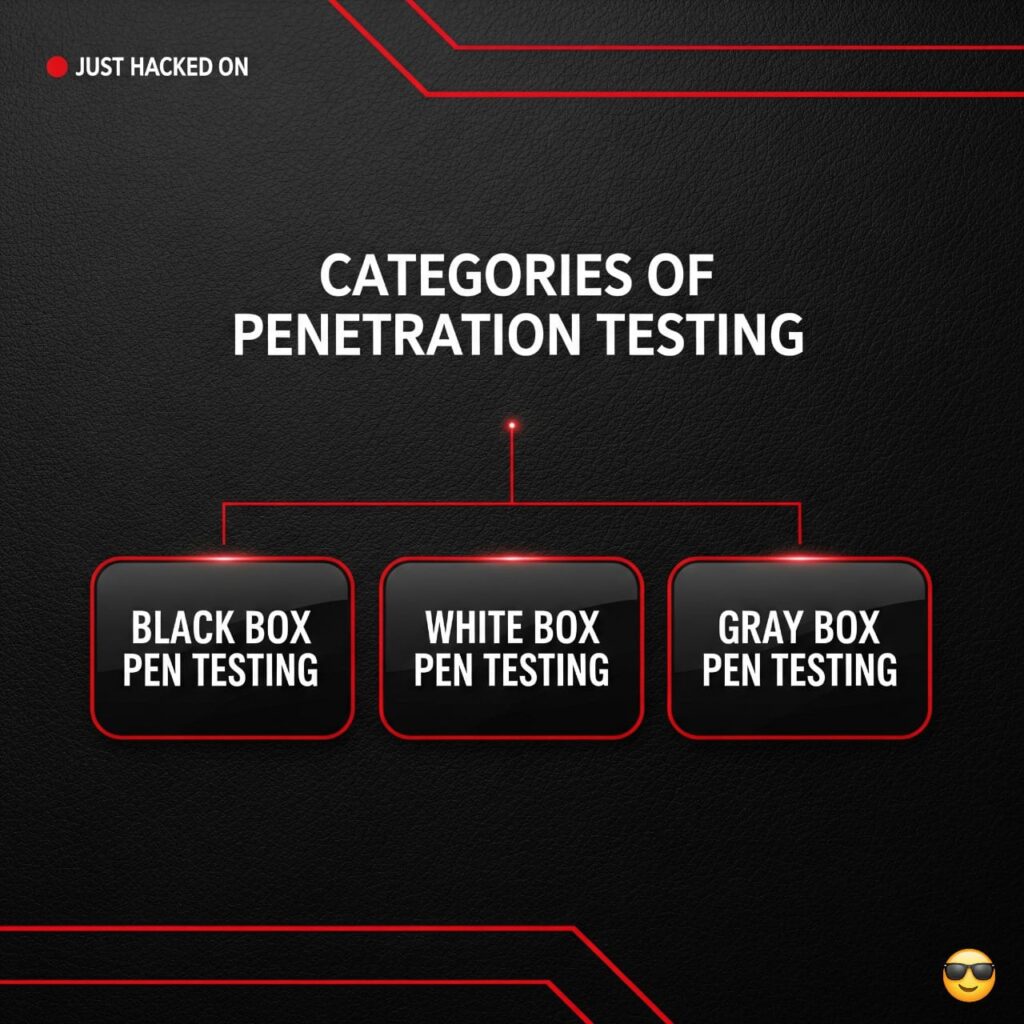
Categories of Penetration Testing – Black / White / Grey Box
What are different categories of penetration testing?
Jab penetration test ka scope define kiya jata hai, usi waqt test ki category ya type bhi decide hoti hai. Penetration test ka poora engagement Black Box, White Box, ya Gray Box ho sakta hai yeh depend karta hai ke organization exactly kya test karna chahti hai aur kis tarah se apni security ko evaluate karwana chahti hai.
Black Box Pen Testing
What is a black box in penetration testing?
Black Box penetration test me target ke baare me bohot kam ya bilkul bhi information provide nahi ki jati.
Agar yeh network penetration test ho, to iska matlab hai ke DMZ, target ka operating system, server version, etc. ka data nahi diya jata sirf IP ranges di jati hain jinko test karna hota hai.
Agar yeh web application penetration test ho, to application ka source code nahi diya jata. Yeh scenario external penetration tests me bohot common hota hai.
White Box Pen Testing
What is a White box in penetration testing?
White Box penetration test me target ka almost sab information provide kiya jata hai.
Network penetration test me applications ka data, unke versions, operating system ka type, etc include hota ha .
Agar yeh web application penetration test ho, to source code provide kiya jata hai jisse hum static/dynamic source code analysis kar sakte hain.
Yeh scenario zyada tar internal ya onsite penetration tests me hota hai, kyun ke organizations ko information leakage ka concern hota hai.
Gray Box Pen Testing
What is a Gray box in penetration testing?
Gray Box penetration test me kuch information di jati hai aur kuch hide ki jati hai.
Network penetration test me organization sirf application ke naam batati hai jo IP ke peeche run ho rahi hain, lekin exact version disclose nahi karti.
Web application penetration test me extra information di jati hai, jaise test accounts, backend server, aur databases ka data .
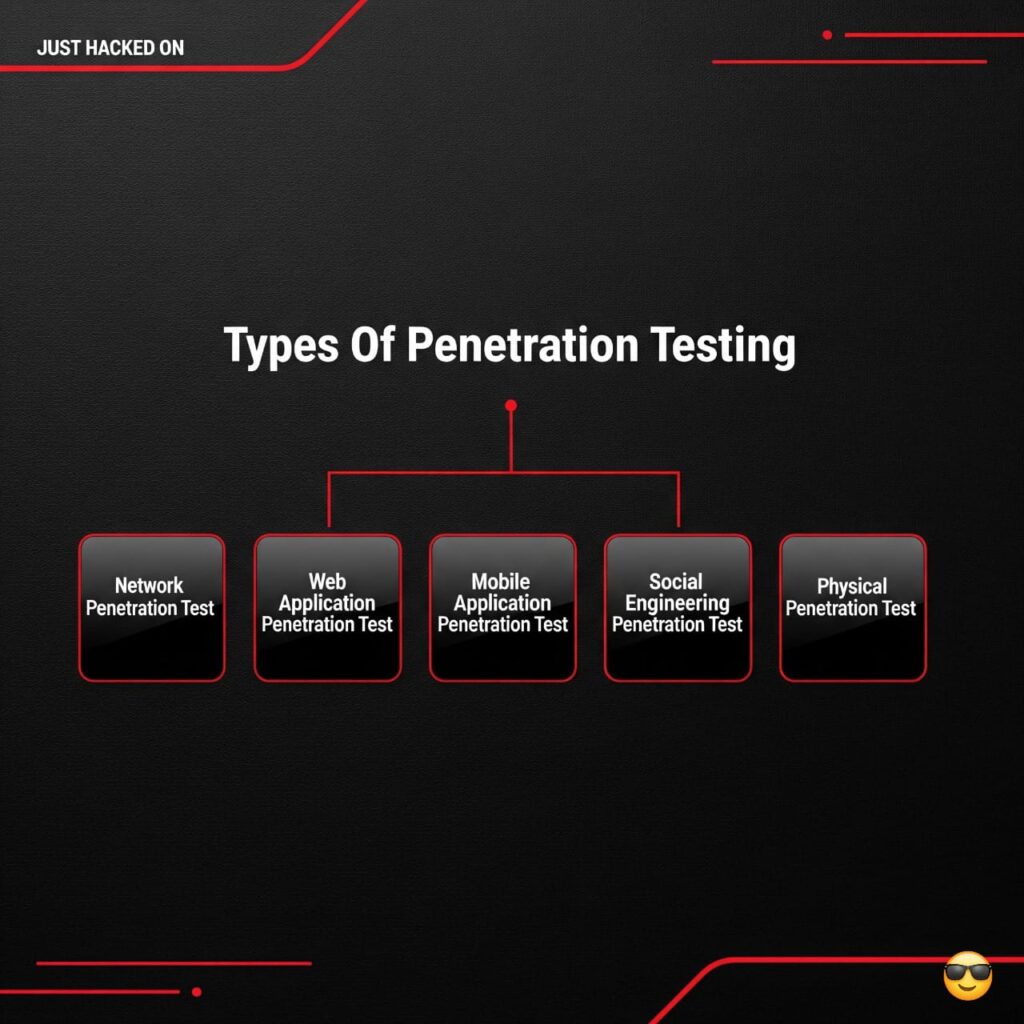
What are the types of penetration testing and Which type’s of penetration test is the most common?
Penetration tests ke kai types hain, lekin niche woh types mention kiye gaye hain jo sab se zyada commonly perform kiye jate hain:
Network Penetration Test
Network penetration test me aap network environment ko potential security vulnerabilities aur threats ke liye test karte ho.
Is test ko do categories me divide kiya jata hai: External aur Internal Penetration Tests.
- External Pen Test: Public IP addresses test ki jati hain.
- Internal Pen Test: Aap internal network ka part ban kar usko test karte ho. Aapko VPN access provide kiya ja sakta hai ya physically organization ke environment me ja kar test karna padta hai, jo engagement rules ke hisaab se decide hota hai.
Web Application Penetration Test
Web application penetration test aaj kal bohot common ho gaya hai, kyun ke applications me critical data store hota hai, jaise credit card numbers, usernames, aur passwords.
Is wajah se yeh type of penetration test network tests se zyada perform kiya jata hai.
Mobile Application Penetration Test
Mobile application penetration test naya aur rapidly growing type hai, kyun ke almost har organization Android aur iOS apps use karti hai apne users ko services provide karne ke liye.
Organizations chahte hain ke unke mobile applications secure hon, taake users apni personal information confidently share kar saken.
Social Engineering Penetration Test
Social engineering test aksar network penetration test ka hissa hota hai.
Is me organization aapko users ko target karne ke liye keh sakti hai. Aap spear phishing attacks aur browser exploits ka use karte hain taake user ko unintentionally actions perform karne par majboor kiya ja sake.
💡 Agar aap in real-world social engineering scenarios ko samajhna aur unhe practically perform karna chahte hain, to Just Hacked On ke saath jud kar aapko hands-on training aur cybersecurity career ke liye professional guidance mil sakti hai.
Physical Penetration Test
Physical penetration test career me rarely perform hota hai.
Is me aapko physically organization ki building me ja kar physical security controls jaise locks, RFID mechanisms, aur access points test karne hote hain.
What should be included in a penetration test report? | How To Write A Penetration Testing Report | Key Elements
Kisi bhi penetration test me, report sab se crucial part hoti hai. Achi report likhna successful penetration testing ki key hai.
Key Factors for a Good Report:
- Simple, Clear, Understandable: Report ko simple aur asan language me likhna chahiye taake har reader samajh sake.
- Presentation: Headers, footers, fonts, aur margins ka consistent style maintain karein. Agar heading ke liye red font use kiya hai, to har heading me wahi style follow karein.
- Organization: Report ka structure well-organized hona chahiye.
- Spelling & Grammar: Har word sahi hona chahiye. Spell-check aur proofreading zaroor karein taake client par negative impression na pade.
- Consistent Voice & Style: Report me ek hi tone aur style maintain karein, taake reader confuse na ho.
- Eliminate False-Positives: Vulnerabilities jo actually present nahi hain unko remove karein. Yeh report ki credibility enhance karta hai.
- Detailed Analysis: Vulnerability ka root cause identify karein aur screenshots ya RAW HTTP requests ke sath evidence provide karein taake developers easily samajh saken.
Understanding the Audience | Who Reads the Report?
Penetration testing report likhte waqt audience ko samajhna bohot zaroori hai. Audience ko teen categories me divide kiya ja sakta hai:
- Executive Class – CEOs aur board members. Technical details me unki interest kam hoti hai. Sirf executive summary aur remediation report padhte hain.
- Management Class – CISOs, CISSPs. Yeh log security policy implement karte hain aur overall strengths, weaknesses, remediation report, aur vulnerability assessment me interest lete hain.
- Technical Class – Security managers aur developers. Yeh log report ka detailed analysis padhte hain aur vulnerabilities ko patch karte hain.
Skills Required to Become a Penetration Tester | How to Become a Penetration Tester | Technical and Soft skills
Penetration tester banne ke liye sirf basic technical knowledge kaafi nahi hota; is field me successful hone ke liye multiple technical aur soft skills ka combination zaroori hai. Neeche un skills ko explain kiya gaya hai:
- Networking Knowledge
Penetration testing ka backbone networking knowledge hai. Aapko TCP/IP, DNS, HTTP/HTTPS, VPNs, firewalls aur routers kaam karne ka tareeqa samajhna zaroori hai. Ye skills aapko systems aur networks ke structure ko samajhne aur unme vulnerabilities detect karne me help karti hain. - Operating Systems Expertise
Aik penetration tester ko Windows, Linux aur macOS jaise operating systems ka detailed knowledge hona chahiye. Linux specially offensive security aur pentesting me extensively use hota hai, isliye command-line tools aur scripting commands me proficiency zaruri hai. - Programming & Scripting Skills
Python, Bash,sql (for sql injection) PowerShell aur kabhi kabhi JavaScript ya C programming ki knowledge penetration testers ke liye bohot important hai. Ye skills aapko automation scripts likhne, exploits customize karne aur vulnerabilities test karne me help karte hain. - Understanding of Security Concepts
Penetration tester ko encryption, authentication, access controls, hashing, web security, and network protocols jaise security concepts ka strong understanding hona chahiye. Ye foundation aapko vulnerabilities samajhne aur unhe exploit karne ka logic provide karta hai. - Knowledge of Penetration Testing Tools
Tools jaise Nmap, Burp Suite, Metasploit, Wireshark, Nessus aur Nikto ka practical knowledge hona chahiye. Ye tools aapko reconnaissance, scanning, exploitation aur reporting tasks efficiently perform karne me help karte hain. - Problem-Solving & Analytical Thinking
Penetration testing me har situation alag hoti hai. Aik tester ko creative aur analytical approach adopt karni hoti hai taake complex security problems identify aur solve kiye ja sakein. - Report Writing Skills
Technical skills ke sath sath penetration testers ko clear aur professional report likhne ka skill bhi zaruri hai. Reports me vulnerabilities, risk assessment aur recommendations ko concise aur understandable language me document karna hota hai. - Continuous Learning & Curiosity
Cybersecurity field constantly evolve hoti hai, naye vulnerabilities aur attack vectors rozana discover hote hain. Is liye penetration tester ka mindset continuously seekhne aur latest security trends ke sath updated rehne ka hona chahiye.
Certifications & Education | Which Certificates Matter?
Penetration testing aur ethical hacking mein professional banne ke liye traditional degrees zaroori nahi hoti. Aap bina kisi formal degree ke bhi ek skilled hacker ban sakte hain, bas practical skills aur real-world experience ka hona bohot zaroori hai. Is field mein age aur conventional education matter nahi karti; is ka sabse best example hai duniya ka youngest hacker, jo sirf 5 saal ki umar mein Microsoft ke Xbox One system mein security flaw discover karke duniya bhar mein mashhoor ho gaya. Uska naam Kristoffer von Hassel hai, aur usne apni curiosity aur self-learning se Microsoft ko ek major vulnerability ke baare mein inform kiya. Aap uski kahani Wikipedia par padh sakte hain: https://uz.wikipedia.org/wiki/Kristoffer_von_Hassel
Hamare education system mein problem ye hai ke schools, colleges aur universities students ko wo skills nahi sikhate jo real industry mein chahiye. Teachers aksar sirf theoretical knowledge provide karte hain jo unhone apne teachers se seekhi hoti hai. Industry ke latest tools, practical security challenges aur real-world attack scenarios ke baare mein students ko guidance nahi milti. Aksar students bas degree hasil kar ke jobs ke liye apply karte hain, lekin unke paas practical skills nahi hoti jo employers expect karte hain. Ye ek circular system ban gaya hai jahan knowledge sirf classroom aur textbooks tak limited rehti hai, real industry knowledge mein gap reh jata hai.
Yahi wajah hai ke Just Hacked On proudly called the Best Online Hacking Academy by our students .
Yahan sirf theoretical knowledge tak limited rehne ke bajaye aapko real-world hacking aur cybersecurity projects me involve kiya jata haibilkul aise jaise aap industry experts ke saath directly kaam kar rahe ho. Humari training ko 100% learners ne recommend kiya hai, aur unke genuine reviews aap student review section me dekh sakte hain
Recommended Certifications (Examples)
Certifications practical skills demonstrate karne ka bohot acha tareeqa hain, lekin har certification equally valuable nahi hai. Jaise ke CEH (Certified Ethical Hacker) bohot popular hai, lekin personally mai suggest nahi karunga ke beginner apna paisa isme waste kare. CEH zyada theoretical hai aur real-world penetration testing mein itni value provide nahi karta jitni advertise ki jati hai. Iske bajaye, aapko wo certifications pursue karni chahiye jo practical knowledge aur hands-on experience provide karein, jaise:
- eJPT (eLearnSecurity Junior Penetration Tester) – Beginner-friendly, practical oriented aur penetration testing ke foundation ke liye perfect.
- CompTIA Security+ – Basic security knowledge aur networking fundamentals ke liye essential.
- CCNA (Cisco Certified Network Associate) – Networking aur network security skills ko strengthen karne ke liye.
- CEH (Certified Ethical Hacker) – Theory-based Certificate ha so agar aapke paas extra paisa hai to certificate le sakte hain, warna sirf modules padh lena kaafi hai, exam dena zaroori nahi.
- OSCP (Offensive Security Certified Professional) – Advanced, hands-on penetration testing certification, industry me highly respected aur real-world challenges cover karta hai.
- CRTP (Certified Red Team Professional) – Red teaming aur Active Directory exploitation ke advanced practical skills ke liye.
Why Cybersecurity Now? Stats & Global Impact
Aaj kal cyber threats ki wajah se duniya bhar mein companies ko bohat bara nuqsan ho raha hai. Amazon rozana karib 750 million cyber attacks detect karta hai, Microsoft ke mutabik unke customers per daily 600 million attacks ho rahe hain, aur Check Point ke mutabik organizations per cyber attacks 47% tak barh chuke hain. Ransomware attacks mein 126% ka izafa hua hai aur har din 560,000 naye malware pieces detect ho rahe hain. 2025 tak global cybercrime se hone wala nuksan 1.5 trillion dollars tak pohanch sakta hai cybersecurityventures.com.
Is liye cybersecurity sirf ek option nahi, balkay ek zarurat ban gayi hai. Chhoti si vulnerability bhi millions ka nuqsan kar sakti hai. Hackers ko hire karne ka faida yeh hota hai ke woh company ke systems aur networks ka detailed analysis karke weakest points uncover karte hain, jo shayad ek normal IT team ko nazar na aayein. Isi liye companies apne systems ka regular penetration testing aur vulnerability assessments karwati hain.
Career Opportunities After Cybersecurity Training & Salary Overview
Cybersecurity field me salaries kaafi depend karti hain aapke experience, skills, aur certifications par. Entry-level ethical hackers aur cybersecurity professionals ki salary $90,000 se $120,000 per year hoti hai, lekin jaise-jaise aap ka experience barhta hai aur advanced certifications hasil karte hain, ye $150,000 se $245,000 tak ja sakti hai (ziprecruiter.com). Senior roles jaise Security Architects aur CISOs aur bhi zyada kama sakte hain, $215,000 ya us se upar (coursera.org, businessinsider.com .
Global level par 3.5 million cybersecurity jobs abhi bhi unfilled hain aur yeh shortage 2030 tak 10 million tak pohanch sakti hai. Yani jobs ki kami nahi, kami hai sirf skilled professionals ki. Matlab agar aap professional ethical hacker ban-na chahte hain, toh demand aur opportunity dono aapke favour me hain.
Agar aap apna cybersecurity career Pakistan me start karna chahte hain, toh aap Just Hacked On, Pakistan ki first online hacking academy, ke saath join karke apna career launch kar sakte hain. Yahan aapko fake ya fancy certificates ke chakkar me nahi phansaya jata; balkay aapko real-world cyber attacks aur advanced hacking techniques sikhai jati hain, jisse aap apne skills aur career dono ko genuinely grow kar sakte hain.
Ab aap par depend karta hai ke aap kahaan se aur kaise apna cybersecurity career start karte hain, lekin start now before it’s too late because time doesn’t wait for your perfect mood , and opportunities always knock for those who are ready to act.
Enroll in Ethical Hacking Training Today | Just Hacked On
Ajj ki digital world ma, jahan har roz new opportunities aur cyber threats samny aa rhy hain, Ethical Hacking ek future-proof field hai. Ye sirf aapka career secure nahi karti, balki aapko ek global level valuable banati hai.
So if you dream to be an Ethical Hacker and Cyber Security Expert in the near future, this is the right time to launch your career with Just Hacked On. Because Time doesn’t wait for your perfect mood, so start now before it’s too late!
Still Confused About Just Hacked On?
Ask me anything related to hacking and cybersecurity . I’m here to help you!
